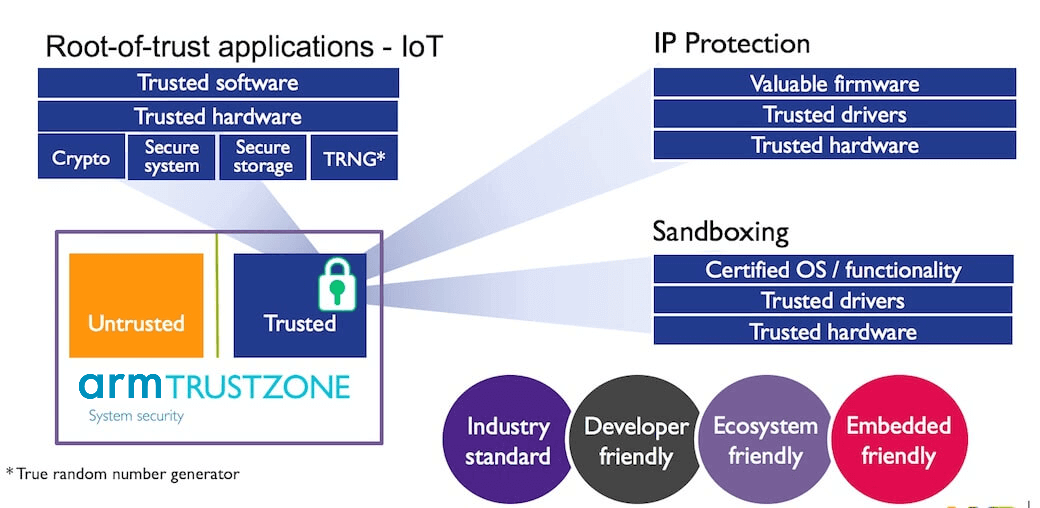
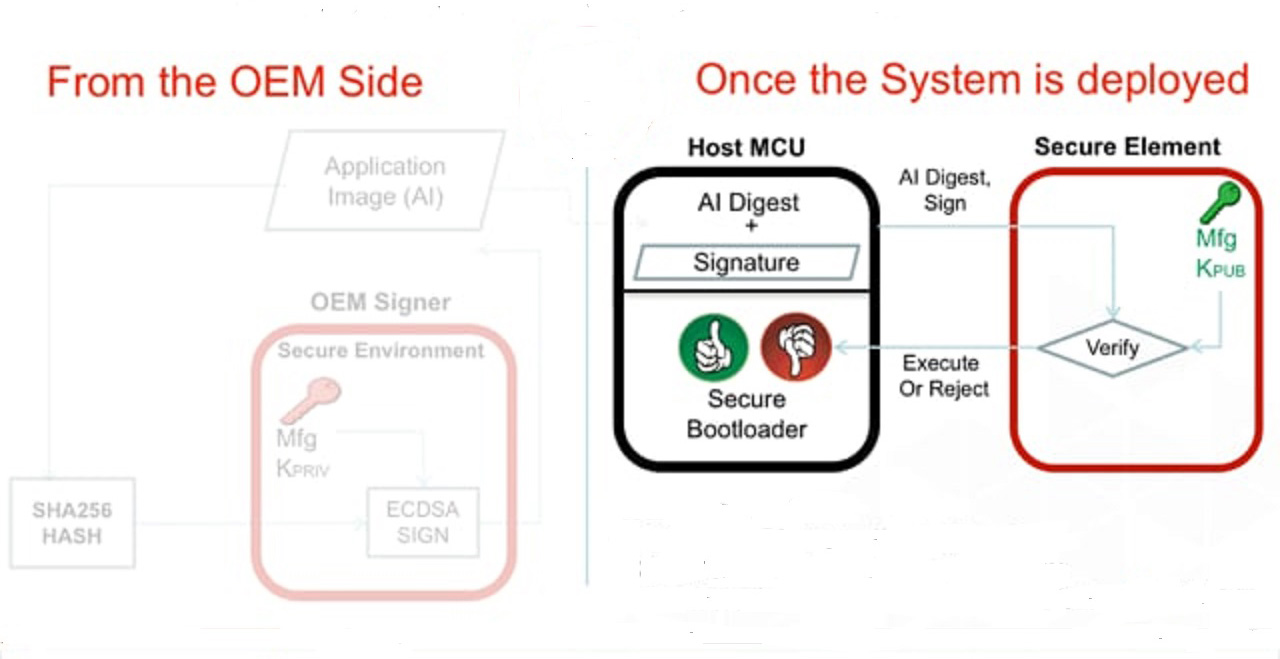
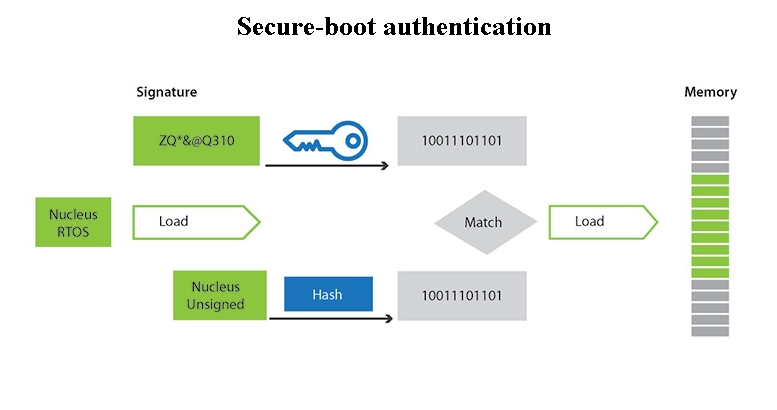
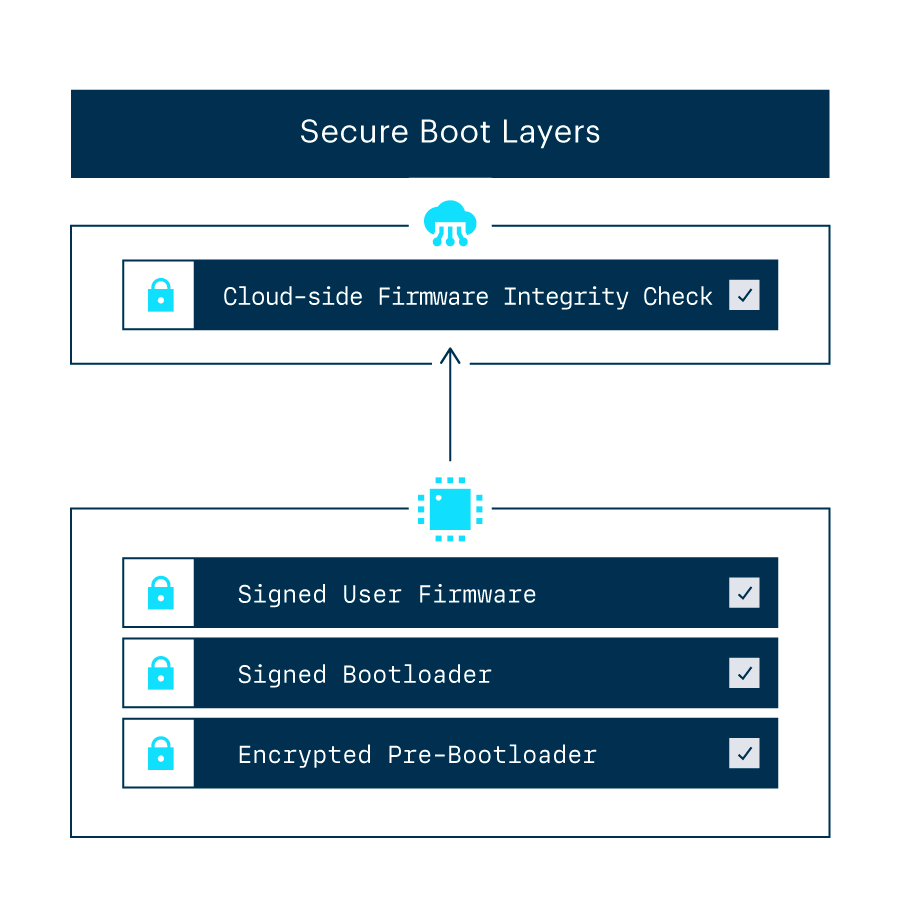
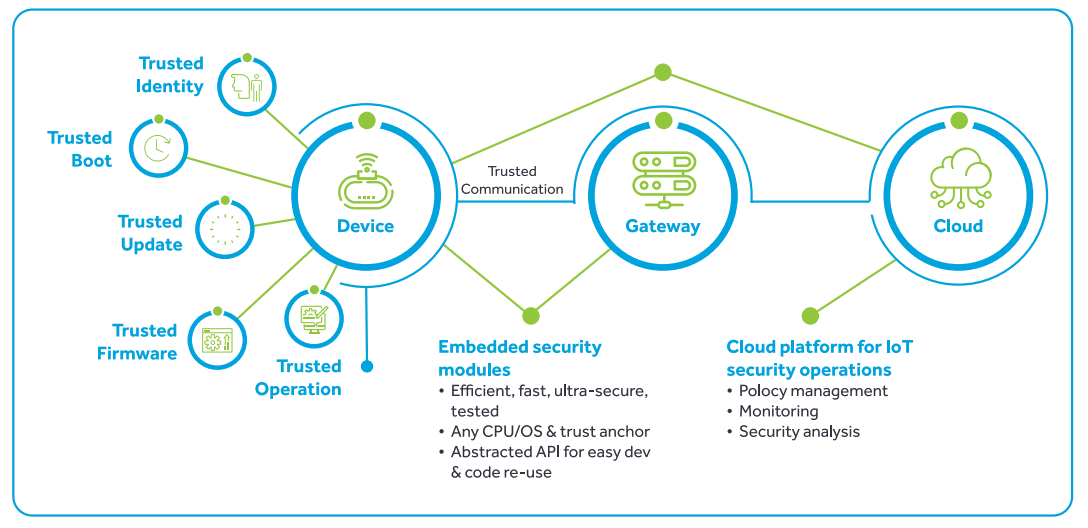
Kontron Introduces Innovative Embedded Security Concept for IoT and Industry 4.0 Environments - Lise-Meitner-Straße, 86156 Augsburg, Germany - Kontron

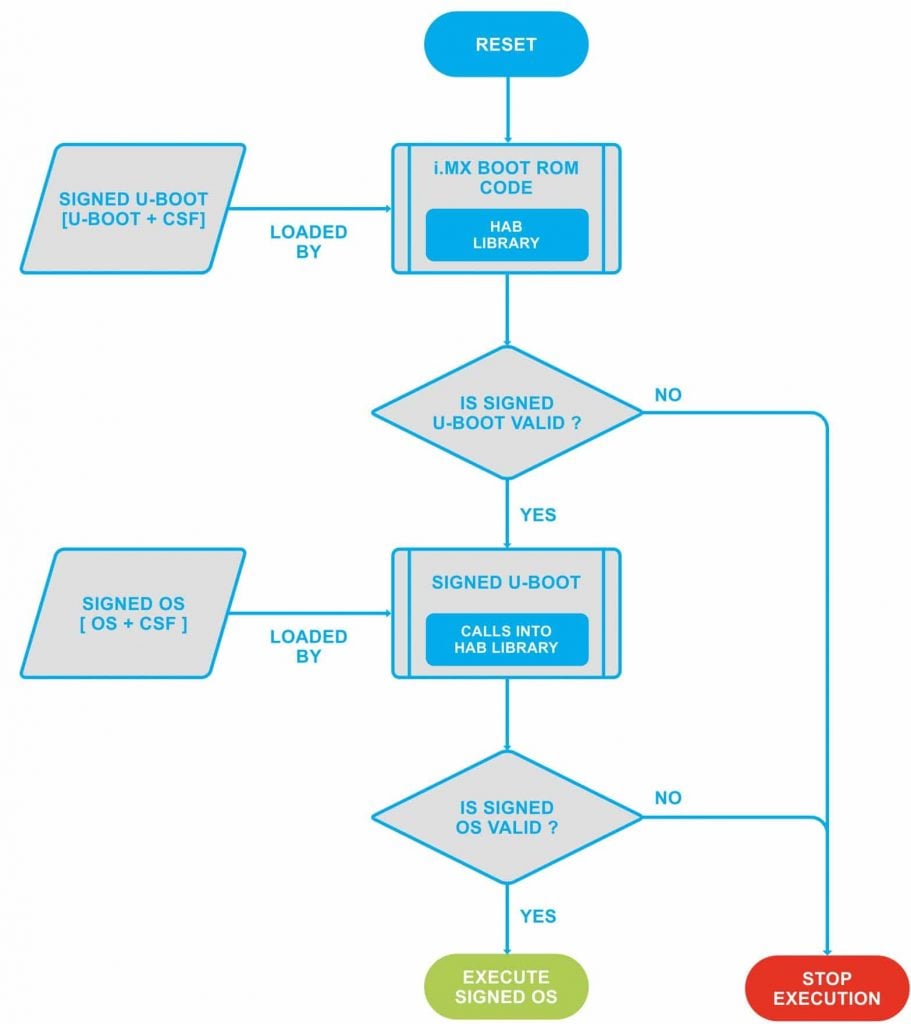
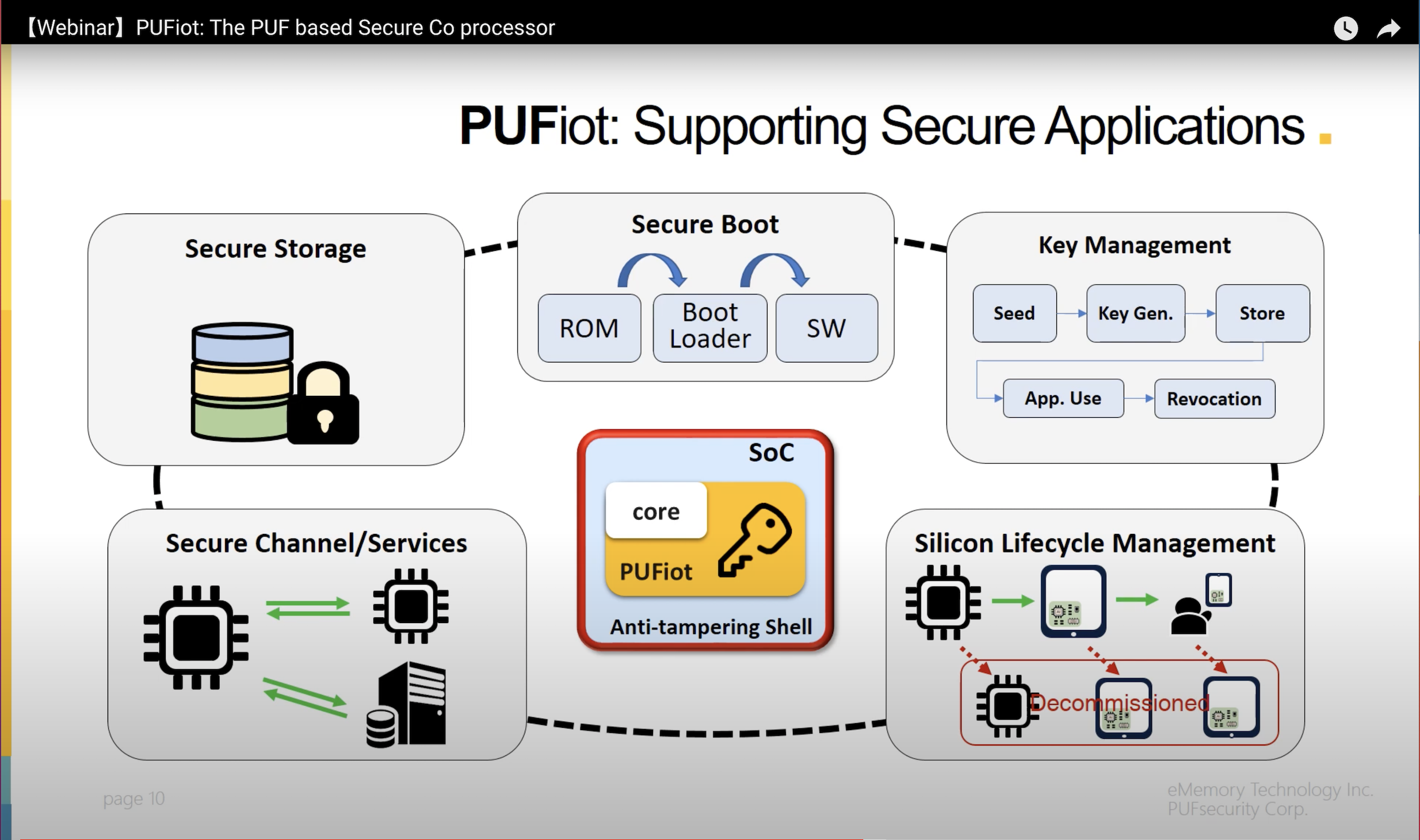
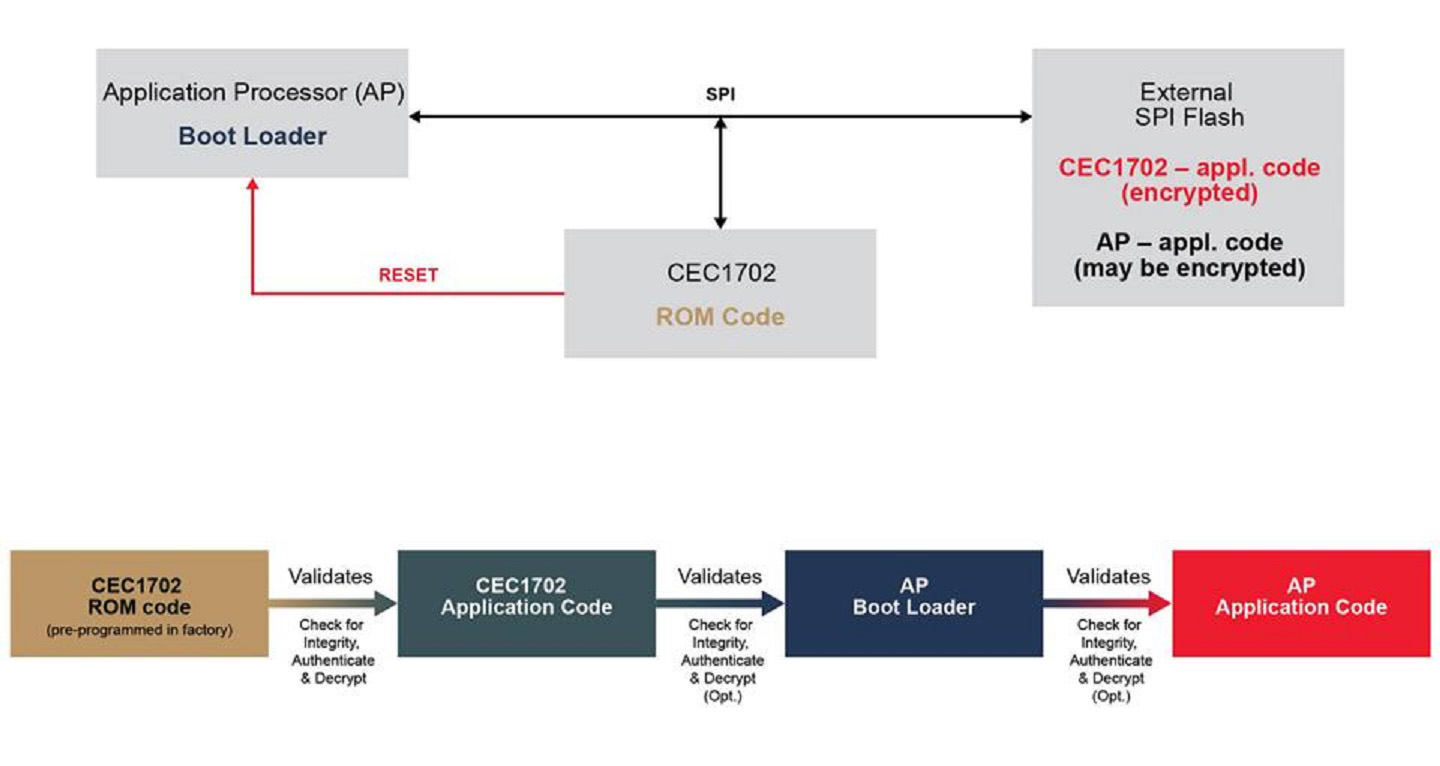
Build highly secure IOT device: secure boot, measured boot and attestation, secure storage etc | by lei zhou | Medium